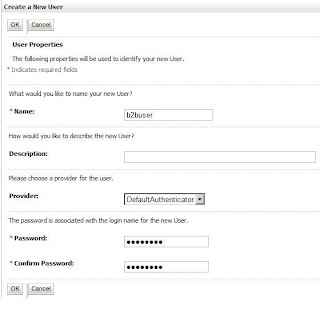
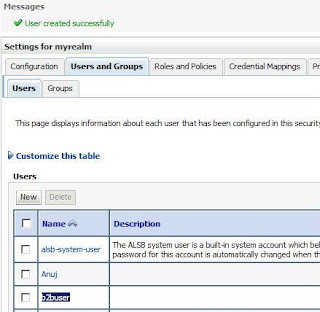
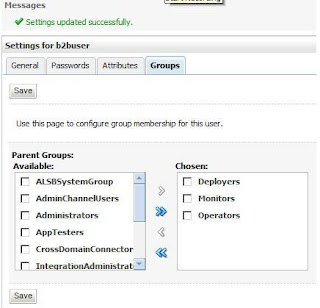
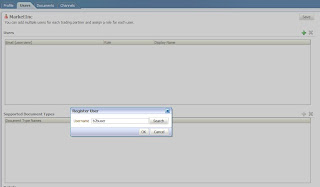
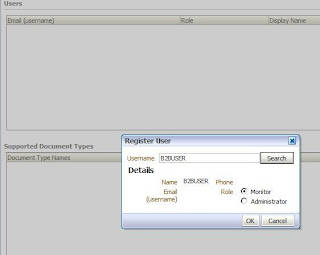
First of all you need digital certificates for enabling security. You may use self-signed certificates for development purpose but it is recommended to use a certificate signed by a trusted certificate-issuing authority (CA) like Verisign, Thwate etc. for higher environments (Test, Pre-prod and Prod)
Step #1 – Generating certificates and Preparing Keystore
As I mentioned earlier that you may use both self-signed and third party issued certificates so I will show you that how to create both.
In Oracle Fusion Middleware 11g stack, we use keytool utility for certificate management. Keytool utility gets shipped with JDK installation itself.
So let us start with certificates generation-
a) Create a directory to store all the certificates and keystore in it. I create one directory D:\b2bkeystores
b) Open a command prompt and execute $MW_HOME/user_projects/domains/
c) Run below command to create a new keystore and generate a new self-signed key-pair (public and private key) in it –
keytool -genkeypair -alias serverCert -keyalg RSA -keysize 1024 -validity 365 –dname "CN=localhost.myCompany.com,OU=Support,O=myCompany,L=Gandhinagar,ST=Gujrat,C=IN" -keypass welcome1 -keystore keystore.jks -storepass welcome1
where localhost.myCompany.com (HostName.Domain) is name of certificate holder, “Support” is organizational unit, “myCompany” is name of the organization , “Gandhinagar” is city/locality, “Gujrat” is State/Province, “IN” is the two-letter country code for this unit
Above command will create a keystore with name “keystore.jks” and it will add a self-signed key-pair in the keystore. You may directly use this self-signed certificate or may get it signed by a third party CA.
Note that the PEM (Privacy Enhanced Mail) format is the preferred format for private keys, digital certificates, and trusted certificate authorities (CAs) and the preferred keystore format is the JKS (Java KeyStore) format in Weblogic server.
Remember that when you use the Keytool utility, the default key pair generation algorithm is Digital Signature Algorithm (DSA) but WebLogic Server does not support DSA so specify another key pair generation and signature algorithm when using WebLogic Server. Here we are using RSA (which stands for Rivest, Shamir and Adleman who first publicly described it) algorithm.
To view the content of the keystore anytime, you may run below command –
keytool -list -keystore keystore.jks -storepass welcome1
If you run above command just after generating the certificates, then below would be shown –
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 1 entry
servercert, Oct 25, 2010, PrivateKeyEntry,
Certificate fingerprint (MD5): CE:38:E1:29:56:72:5F:26:DB:92:27:16:FD:74:5B:DE
If you want to use self-signed certificate (do not want to get your cert signed by any CA) then skip the steps d,e and f
d) Now run below command to generate a CSR (Certificate Signing Request) –
keytool -certreq -v -alias serverCert -file serverCert.csr -keypass welcome1 -storepass welcome1 -keystore keystore.jks
You should see below lines on prompt –
Certification request stored in file
Submit this to your CA
This command will generate a CSR with name “serverCert.csr”. You have to pass this CSR to the third party CA to get it signed by them. The content of the CSR looks like below –
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIBvDCCASUCAQAwfDELMAkGA1UEBhMCSU4xDzANBgNVBAgTBkd1anJhdDEUMBIGA1UEBxMLR2Fu
ZGhpbmFnYXIxEjAQBgNVBAoTCW15Q29tcGFueTEQMA4GA1UECxMHU3VwcG9ydDEgMB4GA1UEAxMX
bG9jYWxob3N0Lm15Q29tcGFueS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAKSt9gLC
TcRU5DynNuAO1Clp/3ygzH1Vdqf4RlQg7p9B5xuNX8ZqhpaN5Ua7pmp9LcLDLUFu3Kzqv6oD7Wa+
nUWvaHKK6Xmz6lclOiapR029FheTx+iZ06qAoi1P/OYu8PVOO+Ldzalz5+dJE9fC51ofRcSJ9xFx
mYsqH9oznUFxAgMBAAGgADANBgkqhkiG9w0BAQUFAAOBgQB560z7cUiaNLI4mN6IqtqfgVsLgp29
86rV+5Xi3PqGgJaVTqpKotR5gMRUMMcvDETdhsY6feTnYkUHlGYXNdLjkGEkIG2qHXiWzZDjxXym
tDIDlToa3FzWEYAyGWshJaoHXzXbicvY3abHcK8ZgADAZgJXjMF8xKMOJ1ua5aI8fw==
-----END NEW CERTIFICATE REQUEST-----
Make sure to take a backup of keystore because once it gets lost/damaged, then you will not be able to recover it and remember that CSR can be imported back into the same keystore (or in it’s backup copy) only after getting signed.
e) Once you get the signed certificate back from third party CA, you have to import it into your keystore along with the certificate of CA who signed your certificate.
Convert the CA certificates and signed certificate received from CA, into PEM format and store them in the same directory where our keystore is (D:\b2bkeystores). As there may be a chain of CA certs so store each and every certificate of the chain, separately.
Now run below command to import the top certificate in the chain (Root CA cert – this must be a self-signed certificate of the CA) –
keytool -importcert -v -noprompt -trustcacerts -alias rootCA -file rootCA.pem -keystore keystore.jks -storepass welcome1
where “rootCA” is the alias of this certificate and “rootCA.pem” is the file which contains the Root CA certificate.
You should see below line if certificate gets added to keystore successfully –
Certificate was added to keystore
Now repeat this step for each and every CA certificate in the certificate chain with different and meaningful alias each time.
For Verisign issued certificates, there may be two CA certs in the chain – Root CA Certificate & Intermediate CA Certificate. So you have to execute above command once for Root CA and after that once for Intermediate CA
f) If you are done with importing the CA certificates then now import the signed reply certificate by using below command –
keytool -importcert -v -alias serverCert -file serverCert.pem -keystore keystore.jks -keypass welcome1 -storepass welcome1
where “serverCert” is the alias of the certificate we generated, “serverCert.pem” is the signed certificate sent by the CA (in PEM format)
If it gets imported successfully then you would see below line –
Certificate reply was installed in keystore
Make sure that you use same alias as what you used while generating certificate and generating CSR (step C and D)
Now if you will run the list command then it will show you all the CA certs you imported as “trustedCertEntry” and the certificate you generated (and got it signed) as a “keyEntry” -
keytool -list -keystore keystore.jks -storepass welcome1
Keystore type: jks
Keystore provider: SUN
Your keystore contains 3 entries
verisignintermediate, Oct 18, 2010, trustedCertEntry,
Certificate fingerprint (MD5): BA:B0:65:B4:3B:9C:E8:40:30:21:7D:C5:C6:CD:3F:EB
serverCert, Oct 18, 2010, keyEntry,
Certificate fingerprint (MD5): 89:C3:19:1D:17:43:76:0A:C3:2E:FB:1F:1F:35:74:D1
verisignroot, Oct 18, 2010, trustedCertEntry,
Certificate fingerprint (MD5): CB:17:E4:31:67:3E:E2:09:FE:45:57:93:F3:0A:FA:1C
g) Run below command to export the public certificate of your server from the kesytore -
keytool -exportcert -alias serverCert -file serverCert.cer -keystore keystore.jks -storepass welcome1
You should see below line on prompt -
Certificate stored in file
Above command will create a file with name “serverCert.cer” which is actually the public certificate of your server which you may share with your Trading Partners.
h) Now import the certificate of all your Remote Trading Partners along with their CA certificates, in the keystore we created. First of all store your TP’s certificate and their respective CA’s certificate in separate files in PEM format (as we did in step ‘e’). After that import all the Root CA certificates (if any) with different alias and then import all the intermediate CA certificates (if any) with different alias and after that import the certificates of all your TP’s with different alias, in the keystore we created.
To add first root CA cert in the keystore, you may use below command –
keytool -importcert -v -noprompt -trustcacerts -alias VerisignRootCA -file VerisignRootCA.pem -keystore keystore.jks -storepass welcome1
where “VerisignRootCA.pem” is a file which holds the VerisignRootCA certificate in PEM format
You should see below lines on prompt –
Certificate was added to keystore
[Storing keystore.jks]
Repeat this process and re-run the above mentioned importcert command for all the certificates.
Step #2 – Configuring Keystore on SOA Server
Now we have to configure the keystore we created on, SOA server. Open the Oracle Weblogic Admin console (by default http://localhost:7001/console) and login into it.
Go to Environment --> Servers and click on the SOA server name (by default soa_server1). Select the checkbox against “SSL Listen Port Enabled” and provide the value for “SSL Listen Port” (by default 8002). Now click on “Save” to save the changes.
Now go to “keystore” sub-tab of “Configuration” tab and click on “Change” button against setting “Keystores” and select the “Custom Identity and Custom Trust” from the “Keystores” dropdown –
Click on “Save” and it will ask you to provide keystore location (absolute path and filename), type and password for both Trust and Identity. Provide the information of kesytore we created in both the sections (Identity & Trust) –
Click on “Save” to save the configuration. Now go to SSL sub-tab, provide the private key alias and password and save the configuration –
Now you are done with the configuration on SOA server. Now to check whether keystore and SSL configuration is behaving properly open Oracle B2B console over HTTPS in any browser (by default https://localhost:8002/b2b where 8002 is SSL listen port of SOA server). If it opens properly, then it means that configuration is working and you may also see the certificate it is presenting on Microsoft Internet Explorer (IE7/IE8)
You may see a warning related to certificate on IE if your certificate has not been signed by a trusted third party CA and you have not installed it yet on windows. You may safely ignore this warning.
Another test case is to access the Oracle B2B default HTTP delivery channel over HTTPS (https://localhost:8002/b2b/httpreceiver) in any web-browser. If it is accessible over HTTPS then on web-browser you should see below text –
B2B Server
B2B Server is ready to accept HTTP messages from the Trading Partner
Step #3 – Configuring Keystore on Oracle B2B Console
Now we have to configure the keystore for Host Trading Partner on Oracle B2B console (by default http://localhost:8001/b2b or http://localhost:8001/b2bconsole)
First of all open the b2b console and login into it. Now navigate to “Profile” tab of Host Trading Partner. Scroll downward and you would see “Key Store” configuration section there. Provide the location of keystore (absolute path with name) and it’s password –
Click on “Save” button to save the configuration –
You are done with the configuration and guess what, you may now use message security and transport security with Oracle B2B 11g!!!