I have already blogged about how to enable SSL on weblogic and configure keystores on Oracle B2B 11g. In this blog I will show you that how to use message security with Oracle B2B.
First of all let me explain that what comes under message security. As part of message security you may-
1. Encrypt an outgoing message so that no one other than the intended recipient can read that message
2. Sign an outgoing message so that receiver can verify that message is actually sent by a trusted party and it has not been modified/manipulated in between the transmission
Encryption is always done using the public key (or public certificate) of the party to whom the message is being sent. Signing is always done using the private key of the party who is sending the message.
Now after understanding this fact that you need a pair of certificates/keys (private key and public key) for message security, you should also understand that two parties communicating with each-other MUST NOT use the same pair of keys or in other words they CAN NOT use the same pair of keys. Both the parties must have different keystores configured on their servers.
I will use two B2B domains and hence two B2B servers – b2bserver1 and b2bserver2 which are configured with two different keystores. Each server has a keystore which holds it’s private key and other server’s public key. I used below keytool commands to create the keystores and export/import each other’s certificate into the respective keystores –
D:\>keytool -genkeypair -alias serverCert -keyalg RSA -keysize 1024 -validity 365 -keypass welcome1 -keystore keystore.jks -storepass welcome1
What is your first and last name?
[Unknown]: localhost.myCompany.com
What is the name of your organizational unit?
[Unknown]: Support
What is the name of your organization?
[Unknown]: MyCompany
What is the name of your City or Locality?
[Unknown]: Hyderabad
What is the name of your State or Province?
[Unknown]: AndhraPradesh
What is the two-letter country code for this unit?
[Unknown]: IN
Is CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN correct?
[no]: yes
D:\>keytool -list -keystore keystore.jks
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 1 entry
servercert, Apr 21, 2011, PrivateKeyEntry,
Certificate fingerprint (MD5): 02:70:1E:A4:CD:86:3C:F3:6B:88:4F:F0:F6:8F:B2:ED
D:\>keytool -exportcert -alias serverCert -file serverCert.cer -keystore keystore.jks -storepass welcome1
Certificate stored in file
D:\>keytool -genkeypair -alias SOAServerCert -keyalg RSA -keysize 1024 -validity 365 -keypass welcome1 -keystore soakeystore.jks -storepass welcome1
What is your first and last name?
[Unknown]: soaserver.myCompany.com
What is the name of your organizational unit?
[Unknown]: Support
What is the name of your organization?
[Unknown]: MyCompany
What is the name of your City or Locality?
[Unknown]: Hyderabad
What is the name of your State or Province?
[Unknown]: AndhraPradesh
What is the two-letter country code for this unit?
[Unknown]: IN
Is CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN correct?
[no]: yes
D:\>keytool -exportcert -alias SOAServerCert -file SOAServerCert.cer -keystore soakeystore.jks -storepass welcome1
Certificate stored in file
D:\>keytool -importcert -trustcacerts -alias SOAServerCert –file SOAServerCert.cer -keystore keystore.jks -storepass welcome1
Owner: CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Issuer: CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Serial number: 4dafd400
Valid from: Thu Apr 21 12:21:44 IST 2011 until: Fri Apr 20 12:21:44 IST 2012
Certificate fingerprints:
MD5: 70:7E:86:6A:03:E8:54:31:04:9D:3B:97:69:50:2E:ED
SHA1: 9C:69:D6:47:27:11:27:BE:72:9E:3A:0C:8E:F0:F0:80:AB:D0:D5:99
Signature algorithm name: SHA1withRSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
D:\>keytool -importcert -trustcacerts -alias serverCert -file serverCert.cer -keystore soakeystore.jks -storepass welcome1
Owner: CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Issuer: CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Serial number: 4dafd232
Valid from: Thu Apr 21 12:14:02 IST 2011 until: Fri Apr 20 12:14:02 IST 2012
Certificate fingerprints:
MD5: 02:70:1E:A4:CD:86:3C:F3:6B:88:4F:F0:F6:8F:B2:ED
SHA1: 6E:49:33:62:BF:76:27:8A:74:44:DB:73:27:69:80:D3:ED:3B:E7:6B
Signature algorithm name: SHA1withRSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
Now configure the keystore keystore.jks on b2b server1 and keystore soakeystore.jks on b2bserver2 –
You can now use these keystores for message security on Oracle B2B.
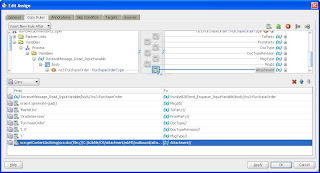
Now configure the MarketInc AS2 channel (Remote TP Channel) with message security on b2bserver1 -
In “Exchange Protocol Parameters” of same channel I also enabled the “Signed and Compressed” setting.
Now configure the OracleServices AS2 channel (Remote TP Channel) with message security on b2bserver2 -
In “Exchange Protocol Parameters” of same channel I also enabled the “Signed and Compressed” setting.
Now configure the agreements on both the servers with respective channels and deploy them.
On B2B server 1-
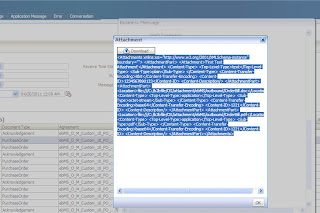
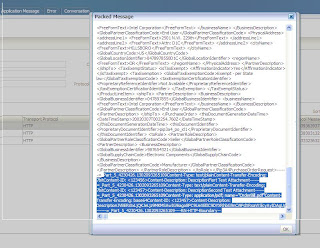
Now you are ready to test your configuration. Push a message to b2bserver1 from middleware and it must sign and encrypt the message before sending it to b2bserver2 and b2bserver2 must be able to decrypt the message and verify the signature. Similarly, b2bserver2 must sign and encrypt the message before sending it to b2bserver1 and b2bserver1 must be able to decrypt the message and verify the signature. In Business Message reports you can see the status of the messages and in wire message report you can see the “Message Digest” and “Digest Algorithm” which proves that message has been signed and when you will try to see the “Packed Message”, you will get below message –
“Data is encrypted and can not be displayed.”
This proves that message has been encrypted. Advanced users can also see the logs and verify whether signing and encryption is happening properly. Go ahead and experiment more with it.
First of all let me explain that what comes under message security. As part of message security you may-
1. Encrypt an outgoing message so that no one other than the intended recipient can read that message
2. Sign an outgoing message so that receiver can verify that message is actually sent by a trusted party and it has not been modified/manipulated in between the transmission
Encryption is always done using the public key (or public certificate) of the party to whom the message is being sent. Signing is always done using the private key of the party who is sending the message.
Now after understanding this fact that you need a pair of certificates/keys (private key and public key) for message security, you should also understand that two parties communicating with each-other MUST NOT use the same pair of keys or in other words they CAN NOT use the same pair of keys. Both the parties must have different keystores configured on their servers.
I will use two B2B domains and hence two B2B servers – b2bserver1 and b2bserver2 which are configured with two different keystores. Each server has a keystore which holds it’s private key and other server’s public key. I used below keytool commands to create the keystores and export/import each other’s certificate into the respective keystores –
D:\>keytool -genkeypair -alias serverCert -keyalg RSA -keysize 1024 -validity 365 -keypass welcome1 -keystore keystore.jks -storepass welcome1
What is your first and last name?
[Unknown]: localhost.myCompany.com
What is the name of your organizational unit?
[Unknown]: Support
What is the name of your organization?
[Unknown]: MyCompany
What is the name of your City or Locality?
[Unknown]: Hyderabad
What is the name of your State or Province?
[Unknown]: AndhraPradesh
What is the two-letter country code for this unit?
[Unknown]: IN
Is CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN correct?
[no]: yes
D:\>keytool -list -keystore keystore.jks
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 1 entry
servercert, Apr 21, 2011, PrivateKeyEntry,
Certificate fingerprint (MD5): 02:70:1E:A4:CD:86:3C:F3:6B:88:4F:F0:F6:8F:B2:ED
D:\>keytool -exportcert -alias serverCert -file serverCert.cer -keystore keystore.jks -storepass welcome1
Certificate stored in file
D:\>keytool -genkeypair -alias SOAServerCert -keyalg RSA -keysize 1024 -validity 365 -keypass welcome1 -keystore soakeystore.jks -storepass welcome1
What is your first and last name?
[Unknown]: soaserver.myCompany.com
What is the name of your organizational unit?
[Unknown]: Support
What is the name of your organization?
[Unknown]: MyCompany
What is the name of your City or Locality?
[Unknown]: Hyderabad
What is the name of your State or Province?
[Unknown]: AndhraPradesh
What is the two-letter country code for this unit?
[Unknown]: IN
Is CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN correct?
[no]: yes
D:\>keytool -exportcert -alias SOAServerCert -file SOAServerCert.cer -keystore soakeystore.jks -storepass welcome1
Certificate stored in file
D:\>keytool -importcert -trustcacerts -alias SOAServerCert –file SOAServerCert.cer -keystore keystore.jks -storepass welcome1
Owner: CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Issuer: CN=soaserver.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Serial number: 4dafd400
Valid from: Thu Apr 21 12:21:44 IST 2011 until: Fri Apr 20 12:21:44 IST 2012
Certificate fingerprints:
MD5: 70:7E:86:6A:03:E8:54:31:04:9D:3B:97:69:50:2E:ED
SHA1: 9C:69:D6:47:27:11:27:BE:72:9E:3A:0C:8E:F0:F0:80:AB:D0:D5:99
Signature algorithm name: SHA1withRSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
D:\>keytool -importcert -trustcacerts -alias serverCert -file serverCert.cer -keystore soakeystore.jks -storepass welcome1
Owner: CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Issuer: CN=localhost.myCompany.com, OU=Support, O=MyCompany, L=Hyderabad, ST=AndhraPradesh, C=IN
Serial number: 4dafd232
Valid from: Thu Apr 21 12:14:02 IST 2011 until: Fri Apr 20 12:14:02 IST 2012
Certificate fingerprints:
MD5: 02:70:1E:A4:CD:86:3C:F3:6B:88:4F:F0:F6:8F:B2:ED
SHA1: 6E:49:33:62:BF:76:27:8A:74:44:DB:73:27:69:80:D3:ED:3B:E7:6B
Signature algorithm name: SHA1withRSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
Now configure the keystore keystore.jks on b2b server1 and keystore soakeystore.jks on b2bserver2 –
You can now use these keystores for message security on Oracle B2B.
Now configure the MarketInc AS2 channel (Remote TP Channel) with message security on b2bserver1 -
In “Exchange Protocol Parameters” of same channel I also enabled the “Signed and Compressed” setting.
Now configure the OracleServices AS2 channel (Remote TP Channel) with message security on b2bserver2 -
In “Exchange Protocol Parameters” of same channel I also enabled the “Signed and Compressed” setting.
Now configure the agreements on both the servers with respective channels and deploy them.
On B2B server 1-
On B2B server2 –
Now you are ready to test your configuration. Push a message to b2bserver1 from middleware and it must sign and encrypt the message before sending it to b2bserver2 and b2bserver2 must be able to decrypt the message and verify the signature. Similarly, b2bserver2 must sign and encrypt the message before sending it to b2bserver1 and b2bserver1 must be able to decrypt the message and verify the signature. In Business Message reports you can see the status of the messages and in wire message report you can see the “Message Digest” and “Digest Algorithm” which proves that message has been signed and when you will try to see the “Packed Message”, you will get below message –
“Data is encrypted and can not be displayed.”
This proves that message has been encrypted. Advanced users can also see the logs and verify whether signing and encryption is happening properly. Go ahead and experiment more with it.